* root: initial rename * web: rename custom element prefix * root: rename external functions with pb_ prefix * root: fix formatting * root: replace domain with goauthentik.io * proxy: update path * root: rename remaining prefixes * flows: rename file extension * root: pbadmin -> akadmin * docs: fix image filenames * lifecycle: ignore migration files * ci: copy default config from current source before loading last tagged * *: new sentry dsn * tests: fix missing python3.9-dev package * root: add additional migrations for service accounts created by outposts * core: mark system-created service accounts with attribute * policies/expression: fix pb_ replacement not working * web: fix last linting errors, add lit-analyse * policies/expressions: fix lint errors * web: fix sidebar display on screens where not all items fit * proxy: attempt to fix proxy pipeline * proxy: use go env GOPATH to get gopath * lib: fix user_default naming inconsistency * docs: add upgrade docs * docs: update screenshots to use authentik * admin: fix create button on empty-state of outpost * web: fix modal submit not refreshing SiteShell and Table * web: fix height of app-card and height of generic icon * web: fix rendering of subtext * admin: fix version check error not being caught * web: fix worker count not being shown * docs: update screenshots * root: new icon * web: fix lint error * admin: fix linting error * root: migrate coverage config to pyproject
2 KiB
| title |
|---|
| Active Directory |
Preparation
The following placeholders will be used:
ad.companyis the Name of the Active Directory domain.authentik.companyis the FQDN of the authentik install.
Active Directory Setup
-
Open Active Directory Users and Computers
-
Create a user in Active Directory, matching your naming scheme
-
Give the User a password, generated using for example
pwgen 64 1. -
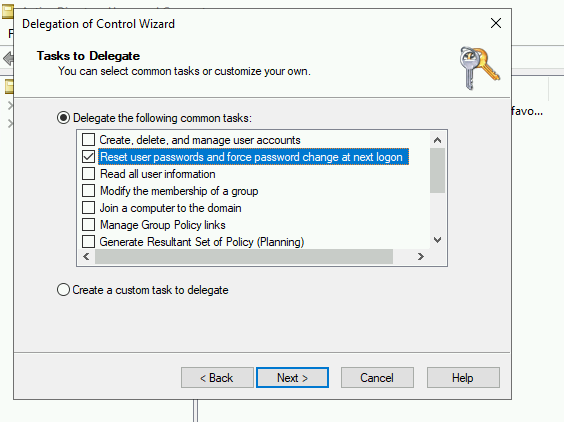
Open the Delegation of Control Wizard by right-clicking the domain.
-
Select the authentik service user you've just created.
-
Ensure the "Reset user password and force password change at next logon" Option is checked.
authentik Setup
In authentik, create a new LDAP Source in Administration -> Sources.
Use these settings:
-
Server URI:
ldap://ad.companyFor authentik to be able to write passwords back to Active Directory, make sure to use
ldaps:// -
Bind CN:
<name of your service user>@ad.company -
Bind Password: The password you've given the user above
-
Base DN: The base DN which you want authentik to sync
-
Property Mappings: Select all and click the right arrow
The other settings might need to be adjusted based on the setup of your domain.
- Addition User/Group DN: Additional DN which is prepended to your Base DN for user synchronization.
- Addition Group DN: Additional DN which is prepended to your Base DN for group synchronization.
- User object filter: Which objects should be considered users.
- Group object filter: Which objects should be considered groups.
- User group membership field: Which user field saves the group membership
- Object uniqueness field: A user field which contains a unique Identifier
- Sync parent group: If enabled, all synchronized groups will be given this group as a parent.
After you save the source, a synchronization will start in the background. When its done, you cen see the summary on the System Tasks page.