* root: initial rename * web: rename custom element prefix * root: rename external functions with pb_ prefix * root: fix formatting * root: replace domain with goauthentik.io * proxy: update path * root: rename remaining prefixes * flows: rename file extension * root: pbadmin -> akadmin * docs: fix image filenames * lifecycle: ignore migration files * ci: copy default config from current source before loading last tagged * *: new sentry dsn * tests: fix missing python3.9-dev package * root: add additional migrations for service accounts created by outposts * core: mark system-created service accounts with attribute * policies/expression: fix pb_ replacement not working * web: fix last linting errors, add lit-analyse * policies/expressions: fix lint errors * web: fix sidebar display on screens where not all items fit * proxy: attempt to fix proxy pipeline * proxy: use go env GOPATH to get gopath * lib: fix user_default naming inconsistency * docs: add upgrade docs * docs: update screenshots to use authentik * admin: fix create button on empty-state of outpost * web: fix modal submit not refreshing SiteShell and Table * web: fix height of app-card and height of generic icon * web: fix rendering of subtext * admin: fix version check error not being caught * web: fix worker count not being shown * docs: update screenshots * root: new icon * web: fix lint error * admin: fix linting error * root: migrate coverage config to pyproject
3.1 KiB
| title |
|---|
| VMware vCenter |
What is vCenter
From https://en.wikipedia.org/wiki/VCenter
:::note vCenter Server is the centralized management utility for VMware, and is used to manage virtual machines, multiple ESXi hosts, and all dependent components from a single centralized location. VMware vMotion and svMotion require the use of vCenter and ESXi hosts. :::
:::warning This requires authentik 0.10.3 or newer. :::
:::warning This requires VMware vCenter 7.0.0 or newer. :::
:::note It seems that the vCenter still needs to be joined to the Active Directory Domain, otherwise group membership does not work correctly. We're working on a fix for this, for the meantime your vCenter should be part of your Domain. :::
Preparation
The following placeholders will be used:
vcenter.companyis the FQDN of the vCenter server.authentik.companyis the FQDN of the authentik install.
Since vCenter only allows OpenID-Connect in combination with Active Directory, it is recommended to have authentik sync with the same Active Directory.
Step 1
Under Property Mappings, create a Scope Mapping. Give it a name like "OIDC-Scope-VMware-vCenter". Set the scope name to openid and the expression to the following
return {
"domain": "<your active directory domain>",
}
Step 2
:::note If your Active Directory Schema is the same as your Email address schema, skip to Step 3. :::
Under Sources, click Edit and ensure that "Autogenerated Active Directory Mapping: userPrincipalName -> attributes.upn" has been added to your source.
Step 3
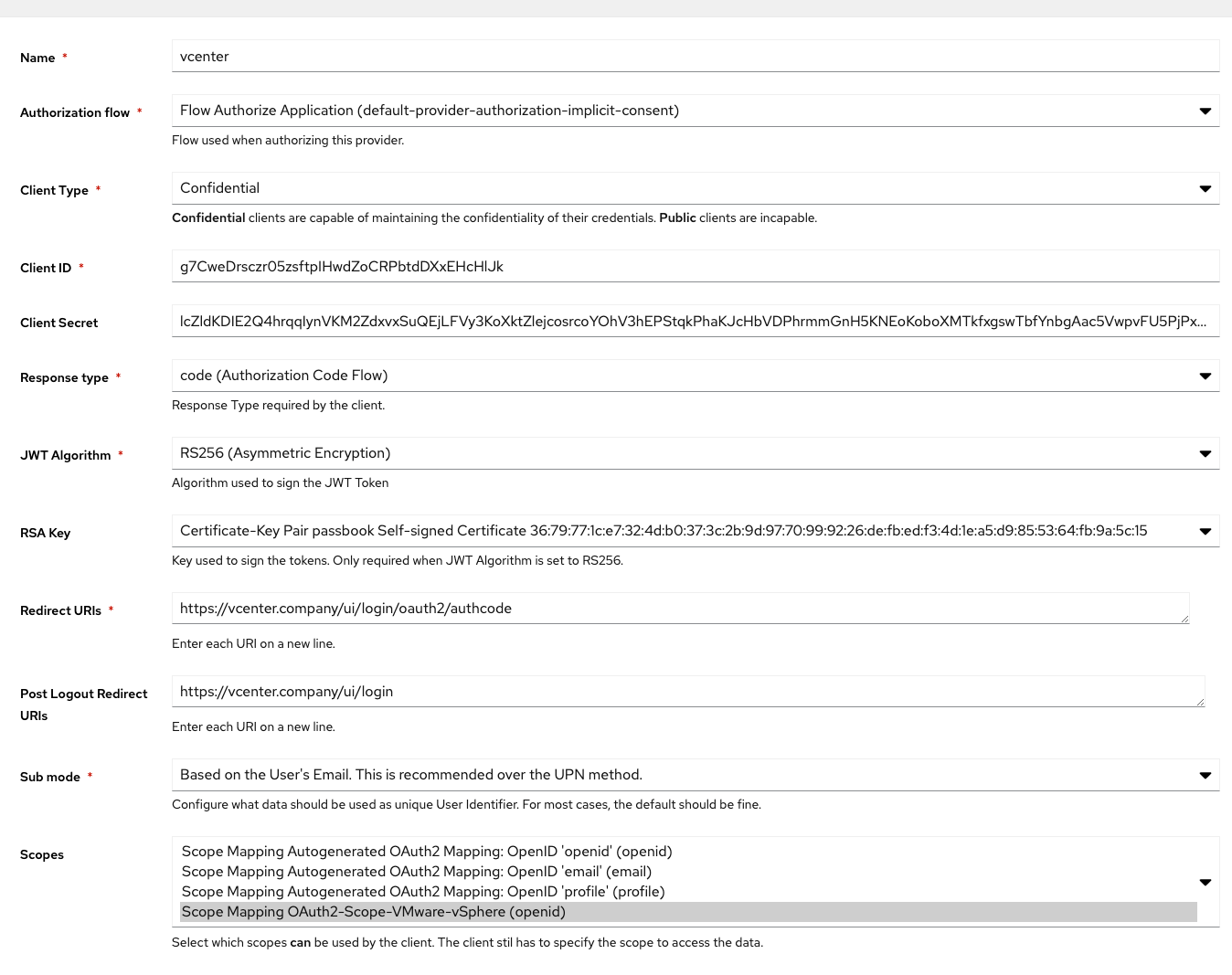
Under Providers, create an OAuth2/OpenID Provider with these settings:
- Client Type: Confidential
- Response Type: code (ADFS Compatibility Mode, sends id_token as access_token)
- JWT Algorithm: RS256
- Redirect URI:
https://vcenter.company/ui/login/oauth2/authcode - Post Logout Redirect URIs:
https://vcenter.company/ui/login - Sub Mode: If your Email address Schema matches your UPN, select "Based on the User's Email...", otherwise select "Based on the User's UPN...".
- Scopes: Select the Scope Mapping you've created in Step 1
Step 4
Create an application which uses this provider. Optionally apply access restrictions to the application.
Set the Launch URL to https://vcenter.company/ui/login/oauth2. This will skip vCenter's User Prompt and directly log you in.
vCenter Setup
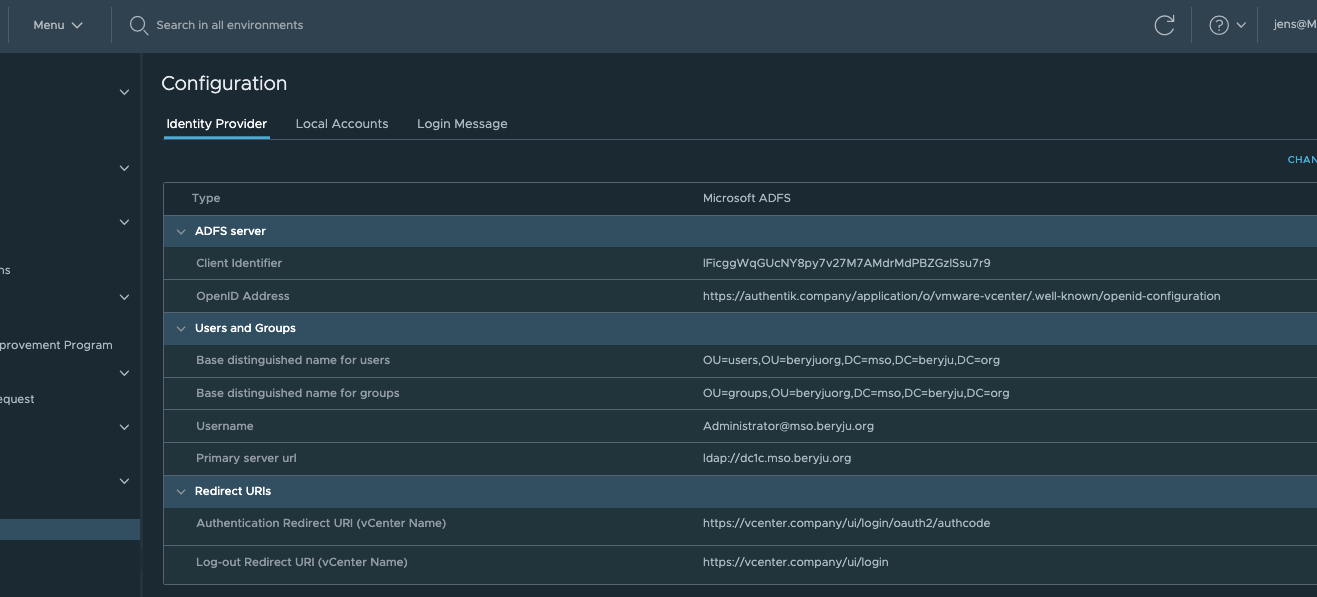
Login as local Administrator account (most likely ends with vsphere.local). Using the Menu in the Navigation bar, navigate to Administration -> Single Sing-on -> Configuration.
Click on Change Identity Provider in the top-right corner.
In the wizard, select "Microsoft ADFS" and click Next.
Fill in the Client Identifier and Shared Secret from the Provider in authentik. For the OpenID Address, click on View Setup URLs in authentik, and copy the OpenID Configuration URL.
On the next page, fill in your Active Directory Connection Details. These should be similar to what you have set in authentik.
If your vCenter was already setup with LDAP beforehand, your Role assignments will continue to work.